Certificate Management
Visit Open Banking Europe for a complete list of QTSPs supplying
Requirements for Qualified Certificates
Annex I of eIDAS requires that QTSP qualified certificates for electronic signatures contain:
- An indication that is identifiable through automated processing that the certificate is a qualified certificated for electronic signature
- A data set that clearly represents the QTSP that issued the qualified certificate, including such information as the:
- Service provider's Member State where the entity is established
- Name and registration number if the provider is a legal person
- Name of the provider if he or she is a natural person.
- Same of the signature or indication is a pseudonym is used
- Corresponding electronic signature validation and electronic signature creation data
Digital signatures are a secure and legally binding means of implementing electronic signatures using asymmetric cryptography, a digital signature is secured and authenticated using three algorithms:
- Key-generating algorithm that randomly selects a private key and its corresponding public key
- Signing algorithm that produces the digital signature from the message and private key
- Signature-verifying algorithm that uses the public key, message and digital signature to confirm the authenticity of the message.
- Information identifying the certificate's period of validity from start to finish
- QTSP's unique certificate identity code
- Issuing QTSP's advanced electronic signature and electronic seal
- Location where the certificate that supports the advanced electronic signature us available free of charge
- An indication, preferable in automated processing form, of where the electronic signature creation data associated with the electronic signature validation data is located in the qualified electronic signature creation device.
If you have a qualified certificate, the Elavon dashboard offers
Using the Dashboard to Manage Certificates
Under the Certificate Management dashboard setting, you add and maintain your eIDAS-qualified for secure communications with Elavon. Your organization needs to install the certificate on its web server to initiate a secure session with browsers. Once a secure connection is established, all web traffic between the web server and the web browser is secured. Hence, when a certificate is successfully installed on your server, the application protocol HTTP changes to HTTPS, where the ‘S’ stands for ‘secure’. You obtain a certificate from a .
Typically, an applicant for a digital certificate will generate a key pair consisting of a private key and a public key, along with a certificate signing request (). Key pair and CSR generation are usually done on the server or workstation where the certificate will be installed, and the type of information included in the CSR varies depending on the validation level and intended use of the certificate. Unlike the public key, the applicant’s private key is kept secure and should never be shown to the CA (or anyone else).
After generating the CSR, you will need to send it to a CA, who independently verifies that the information it contains is correct and, if so, digitally signs the certificate with an issuing private key and sends it back to you. Once you have the signed certificate, you're ready to upload it for use with Elavon.
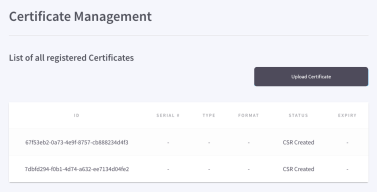
Again, use the dashboard's Certificate Management setting to upload a certificate, which will then appear in your List of all registered Certificates, indicating its ID, SERIAL #, TYPE, FORMAT, STATUS, and EXPIRY.
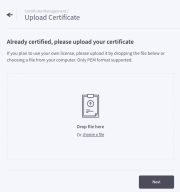
To upload a certificate:
- Click Upload Certificate, then drop the file into the capture zone or click choose a file to browse for and select it from a directory on your computer, then click Next.
-
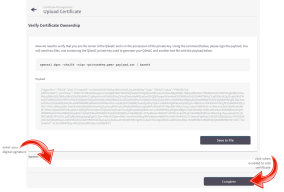
Enter (copy-paste) your digital Signature to verify that you are the owner of the certificate.
-
Click Complete to finish adding the certificate.
- Distinguished Name () of the entity that owns the public key
- DN of the entity that issued the certificate
- Period of time during which the certificate is valid
- The public key itself (e.g., 3048 0241 00C9 18FA CF8D EB2D EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F 922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001).
See Security Tip (ST04-018) to learn more about how digital signatures work.
- When successfully added, your uploaded certificate appears in the list, ready to use.
Certificates that follow the X.509 standard contain a data section and a signature section. The data section includes: